Author: Joseph Jachimiec, Security Administrator
With over 9,300 security breaches recorded since 2005, and a whopping 10.4 billion records estimated stolen (source: privacyrights.org), it’s essential for businesses to follow a reliable security framework to guide their information security programs.
One such framework is the Payment Card Industry Data Security Standard (PCI DSS).
In this post, we’ll take a quick look at how PCI DSS started. We’ll also define “cardholder data” and touch on the 12 requirements of the standard.
PCI DSS Overview and History
PCI DSS was introduced in 2004 by the five major credit card companies: American Express, Discover Financial Services, JCB, MasterCard, and Visa.
Before joining forces, each company had internal security programs to combat rampant credit card fraud and breaches. They formed the Payment Card Industry Security Standards Council (PCI SSC) to establish a common standard. Additionally, they needed to solve the interoperability problems of individual programs.
From this group, the PCI Data Security Standard was born. It’s aim? To reduce credit card fraud and to give guidance for controls around cardholder data. To this day, the PCI Council acts as the governing body for the PCI Standard.
PCI DSS has been through many iterations since version 1.0 in 2004. Major updates to the standard were released in October 2010 (version 2.0) and November 2013 (version 3.0). At the time of this writing, version 3.2.1 is the most current, released in May 2018.
The PCI DSS applies to any entity that accepts, processes, stores, or transmits cardholder data, including merchants and service providers.
What is Cardholder Data?
In short, cardholder data (and sensitive authentication data) is the good stuff that thieves are after. Here’s a breakdown from the version 3.2.1 documentation:
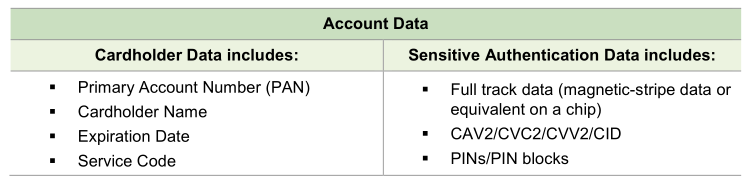
Interesting fact: although PCI DSS permits cardholder data storage, sensitive authentication data storage is not allowed, even if encrypted.
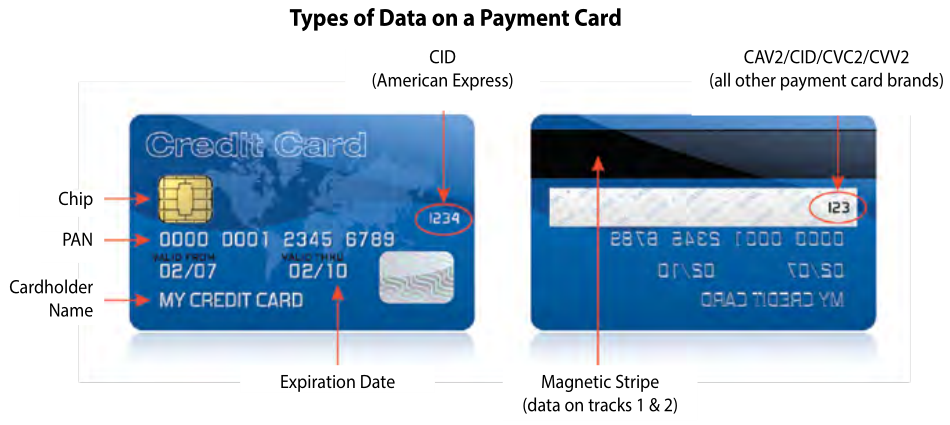
To show where this data lives on a typical credit card, take a look at this image from the PCI DSS Quick Reference Guide:
The PCI DSS Requirements
The PCI Data Security Standard breaks down into 12 compliance requirements within six goals:
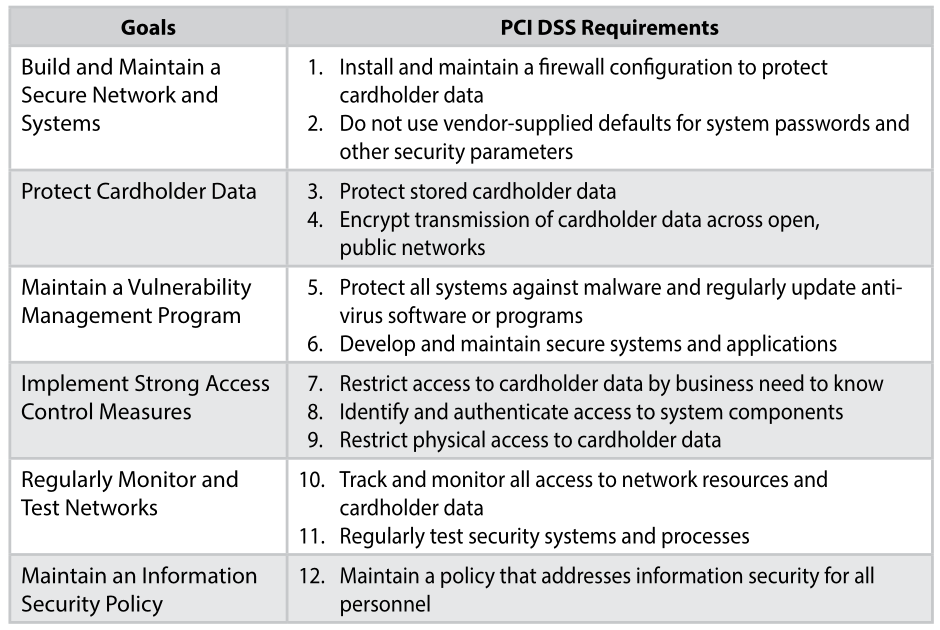
As you can see, each requirement is a significant security undertaking for any company. When met though, these requirements mirror security best practices, protect cardholder/sensitive authentication data, and lead toward PCI DSS compliance and certification.
The PCI DSS documentation lays out guidance steps for each requirement. It also unveils the testing procedures that the PCI Qualified Security Assessor (PCI QSA) performs to confirm the requirements are in place. Consider it your PCI cheat sheet!
Conclusion
At Nahan, PCI DSS is just one of the security frameworks that guide our information security program. We’re proud to be PCI Compliant and Certified since 2016. Our annual PCI QSA audit verifies that we’re meeting all PCI DSS requirements to protect cardholder data.
To learn more about our PCI DSS compliance and to see our Attestation of Compliance, contact us today.
Joseph Jachimiec is a security, IT, and marketing professional. As the Security Administrator at Nahan, he heads up our information security program and is the go-to guy for our customer/third-party security audits and PCI, SOC 2, and HIPAA compliance initiatives. In his spare time, he dreams about what it would be like to have more spare time.
Image by TheDigitalWay from Pixabay

